Android malware on the rise, but Google says the threat’s overblown
Nov 21, 2011 — by Eric Brown — from the LinuxDevices Archive — viewsMcAfee says malware targeting Android devices jumped nearly 37 percent in the third quarter compared to 2Q 2011. This report follows others regarding the growth in Android malware — including a Juniper Networks claim that there's been a 472 percent increase — but Google's Chris DiBona counters that the threat of serious viruses spreading between Android devices is overblown.
Antivirus technology security firm and Intel subsidiary McAfee released a report on third quarter mobile malware, claiming that malware targeting Android devices jumped nearly 37 percent in the third quarter compared to 2Q 2011. Almost all new mobile malware that appeared in the third quarter is designed to attack Android devices, says the report. Total mobile malware share, however, is still dominated by Symbian, says McAfee (see chart below).
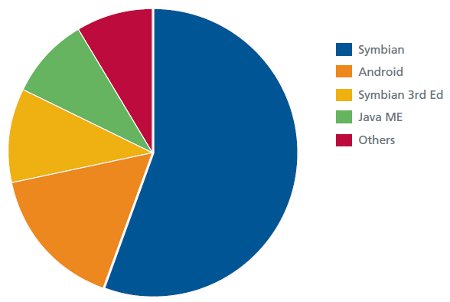
Total mobile malware by OS, 3Q 2011
Source: McAfee [PDF]
(Click to enlarge)
Overall, one of the most popular types of malware for the quarter is said to be an SMS-sending Trojan that collects personal information and steals money. Another new method of stealing user information is to record phone conversations and forward them to the attacker, says the company.
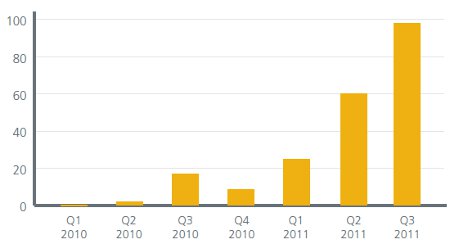
Android malware by quarter, 2011
Source: McAfee [PDF]
(Click to enlarge)
The number of malware samples identified in September increased by 28 percent compared to all known Android malware samples, says Juniper Networks. October is said to have seen a 110 percent increase in malware sample collection over the previous month. Some 55 percent of known Android malware samples act as spyware, while some 44 percent are SMS Trojans, the company adds.
Android is an easy target, claims Juniper Networks, because of its open source nature and Google's skimpy controls over apps published on Android Market.
"Android's open applications store model, which lacks code signing and an application review process that Apple requires, makes it easy for attackers to distribute their malware," says Juniper Networks. There's "no upfront review process, no one checking to see that your application does what it says" on Android Market, the company warns.
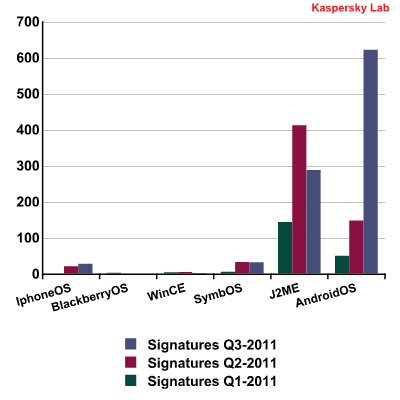
Mobile malware new signatures in 2011
Source: Kaspersky Lab
Is the Android malware threat overblown?
Security and technology analyst Richi Jennings responded to the Juniper Networks claims on an HP blog, claiming the 472 percent claim for Android malware growth since July is both questionable and misleading.
While Juniper Networks points to Google's lax oversight of Android Market as key to the rise in malware, Jennings points out that Google oversight of Android Market has become much stricter than is implied by Juniper Networks. And the lack of "code signing" alleged by the research firm has nothing to do with malware, adds Jennings.
More importantly, the vast majority of Android malware is found not in Android market, but in thid-party Chinese app stores that are rarely visited by Android users, argues Jennings. And the malware usually requires more than a download to activate, he writes.
"Neither do [typical Android users] delve into scarily-named settings menus, uncheck the box that restricts their phone to the Android Market, and ignore the dire warning that then gets displayed," he adds.
Continues Jennings, "Basically, this statistic is, if not a damn lie, then at least extremely carefully worded to imply that the Android Market is riddled with malware, while not actually saying so."
Google responds
 Meanwhile, Google open source Guru Chris DiBona posted a Google+ blog entry responding to a recent "article about open source" and the malware threat that "drives me nuts." DiBona (pictured) argues that what Android users need to be warned about is not so much malware as the overblown threats from security vendors and analysts.
Meanwhile, Google open source Guru Chris DiBona posted a Google+ blog entry responding to a recent "article about open source" and the malware threat that "drives me nuts." DiBona (pictured) argues that what Android users need to be warned about is not so much malware as the overblown threats from security vendors and analysts.
It is unclear if it was the Juniper Networks report that triggered DiBona's Nov. 16 blast, but DiBona argues that an open source platform like Android is actually more difficult for malware to infect in the long run because the community tends to isolate and avoid problematic app publishers.
In addition, DiBona writes that analyst warnings over viruses that spread from phone to phone without requiring an app download are "not probable" on modern smartphone platforms due to "the user sandboxing models and the nature of the underlying kernels."
Continues DiBona, "If you read an analyst report about 'viruses' infecting iOS, Android or RIMim, you now know that analyst firm is not honest and is staffed with charlatans."
This article was originally published on LinuxDevices.com and has been donated to the open source community by QuinStreet Inc. Please visit LinuxToday.com for up-to-date news and articles about Linux and open source.