Android Trojan found in alternative app markets
Feb 24, 2011 — by LinuxDevices Staff — from the LinuxDevices Archive — 7 viewsA new Android Trojan is being repackaged in popular Android apps and distributed through app markets and forums serving Chinese-speaking users. Mobile security firms NetQin and Lookout Mobile Security have both issued alerts regarding the “BD.HongTouTou” Trojan, which has been found in repackaged titles like “RoboDefense.”
Two variants of the latest Android malware have been spotted in two alternative application markets that primarily target Chinese customers, according to security researchers. Dubbed "BD.HongTouTou.A" and "BD.HongTouTou.B," the latest Trojan variants are repackaged inside popular Android apps and distributed through alternative app markets and forums, NetQin, a Chinese mobile security service provider said on Feb. 22.
The malware has been found in the popular game "RoboDefense" and a number of wallpaper apps, according to NetQin. Even though these apps have been repackaged with the Trojan and are being distributed in alternative markets, "the original versions available in the official Google Android Market have not been affected," Lookout Mobile Security, another mobile security firm, said on Feb. 15 in its initial alert.

Composition of example third-party Android app sources
Source: App Genome Project, Lookout Mobile Security
(Click to enlarge)
When the app hosting HongTouTou starts, it sends encrypted data containing the device's IMEI and IMSI information to a remote host. The malware receives a set of search engine targets and a set of search keywords from the remote host, which it uses to emulate a series of search queries, Lookout said.
The malware also simulates looking at the top search results and clicking on specific results. As far as the search engine is concerned, these queries appear to be legitimate searches performed by a mobile user.
"The virus is also capable of analyzing the user's private information using keywords," NetQin said. In addition, it has the ability to download an Android package file and install it, although Lookout researchers said they have not yet seen the Trojan attempt to do so.
The APK appears to have the ability to monitor SMS conversations and insert specific keywords into the conversation, Lookout researchers wrote.
Repackaging repercussions
Lookout security researchers identified 14 instances of HongTouTou repackaged inside Android apps, the company said on its blog. In a recent apps market report, Lookout analyzed two different alternative markets that target Chinese customers and found nearly 11 percent of the redistributed apps that existed on the official Google market were either repackaged or not submitted to the alternative market by the original developer.
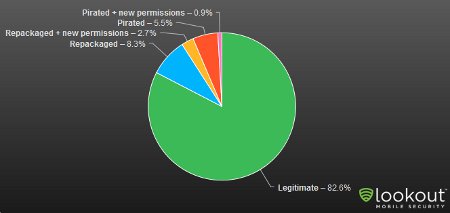
Analysis of pirated and redistributed Android apps
Source: App Genome Project, Lookout Mobile Security
(Click to enlarge)
Of the redistributed apps, nearly a quarter requested more permissions than the original app did, Lookout said. The additional permissions requested by repackaged apps include access to location, contact information, phone state, Internet access, and the ability to make phone calls.
In December 2010, Lookout discovered a sophisticated Trojan named "Geinimi" in an alternative app store in China that could compromise a significant amount of personal data on a user's phone and send it to remote servers.
A Feb. 23 eWEEK report on mobile security by Brian Prince cites a Kapersky Lab claim that there are there are "probably more than 2,000 pieces of mobile malware in the wild today." The report sums up recent mobile security announcements, including a mobile security push by McAfee, as well as Kapersky Lab adding Android and BlackBerry support to its new Kaspersky Mobile Security 9 software.
Availability
More information on NetQin may be found at the NetQin website. Lookout Security's Android security report may be found on its App Genome Project page.
Fahmida Rashid is a writer for our sister publication eWEEK.
This article was originally published on LinuxDevices.com and has been donated to the open source community by QuinStreet Inc. Please visit LinuxToday.com for up-to-date news and articles about Linux and open source.