Android Market being targeted by malware
Mar 2, 2011 — by LinuxDevices Staff — from the LinuxDevices Archive — 108 viewsGoogle will soon pull dozens of “DroidDream Trojan” malware apps from its Android Market, which is now getting hit by malware that has previously targeted third-party app stores. Also this week, a compromised version of the “Steamy Windows” Android app has shown up on a Chinese third-party app hosting site.
Google is preparing to remove numerous applications laced with malware from Android Market, underscoring the threat of rogue applications infiltrating the company's mobile marketplace. According to Lookout Mobile Security, more than 50 applications released under the developer names "Myournet", Kingmall2010," and "we20090202" were infected with the DroidDream Trojan and will soon be removed by Google. A complete list of the affected apps is available on the Lookout blog linked to above.
An update to the Lookout report states, "We originally reported that Google removed the apps from devices, but we recently learned that the remote removal system has not yet been engaged for these applications because they are under active investigation."
An analysis by security company Kaspersky Lab found that the DroidDream Trojan attempts to gather a variety of information, including product ID, device type and user ID data. After swiping the information, the Trojan will upload it to a remote server. Unlike most of the other samples seen so far, there is no attempt at sending or receiving premium-rate SMS messages, the firm said.
"DroidDream is packaged inside of seemingly legitimate applications posted to the Android Market in order to trick users into downloading it, a pattern we've seen in other instances of Android malware such as Geinimi and HongTouTou," Kevin Mahaffey, CTO of Lookout, told our sister publication eWEEK.
Unlike previous instances of malware that were only available in alternative app markets targeted towards certain countries, DroidDream was available in the official Android Market - something that indicates a growing need for consumers to be aware of the apps they download and actively protect their smartphones, Mahaffey said.
It is not the first time however that Google has pulled suspicious apps from its marketplace. In December, Google yanked several apps that used the name of various banks, including Chase, Sun Trust, and Bank of America without permission. The applications were removed not long after financial institutions began warning customers that rogue Android apps were trying to gain access to their information.
Story gets steamier
 Earlier this week, researchers at Symantec reported a compromised version of an Android app called Steamy Window (pictured) that had been discovered on a Chinese third-party app hosting site. The app was infected with a Trojan Symantec calls Android.Pjapps, and is thought to have been designed to push advertisement campaigns and "reap the benefits from compromised devices using third-party, premium-rate services."
Earlier this week, researchers at Symantec reported a compromised version of an Android app called Steamy Window (pictured) that had been discovered on a Chinese third-party app hosting site. The app was infected with a Trojan Symantec calls Android.Pjapps, and is thought to have been designed to push advertisement campaigns and "reap the benefits from compromised devices using third-party, premium-rate services."
"The Android.Pjapps code is well written and as such, can be easily inserted into any number of otherwise legitimate apps by someone who knows what they are doing," explained Vikram Thakur, principle security response manager at Symantec.
"A couple of examples of where we're seeing this malicious code (are) in a compromised version of the Steamy Window app and also in a compromised video player app," continued Thakur. "However, we expect to see quite a few more legitimate looking apps over the coming days propagating this threat via unregulated Android marketplaces."
Once Android.Pjapps is installed, an attacker can initiate the download and installation of other applications as well; however, completing the installation of another app would require the phone owner's permission, Thakur said.
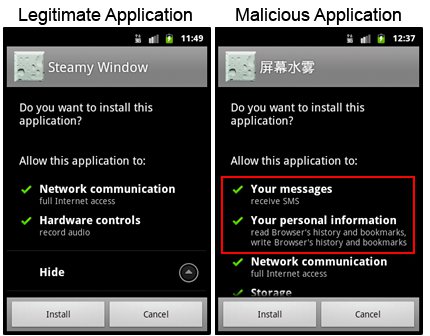
Legitimate Steamy Window (left) and malware version (right)
"One of the important observations here is that it is likely that these are not the only live malware in the Android Market," blogged Tim Armstrong, malware researcher for Kaspersky Lab. "Kaspersky recommends that you always check all the permission requests that an application is requesting at install time."
Brian Prince is a contributor to our sister publication eWEEK.
This article was originally published on LinuxDevices.com and has been donated to the open source community by QuinStreet Inc. Please visit LinuxToday.com for up-to-date news and articles about Linux and open source.