Up to a million Android users affected by malware, says report
Aug 3, 2011 — by LinuxDevices Staff — from the LinuxDevices Archive — viewsAndroid malware affects from 500,000 to 1 million smartphone users, who are two and a half times as likely to encounter malware today as six months ago, according to a Lookout Mobile Security analysis. Meanwhile, security experts are debating the threat of an Android Trojan that records one's phone calls.
Android device owners have plenty to be wary of on the security front, according to a new report from Lookout Mobile Security. Android users are 2.5 times more likely to be affected by malware today than they were six months ago, the firm said in its new 2011 Mobile Threat report. Moreover, anywhere from 500,000 to 1 million users were said to have been impacted by malware on their Android smartphone or tablet this year.
In addition, three out of 10 Android gadget owners are likely to encounter a web-based threat on their device each year, says the report, released in conjunction with this week's Black Hat security conference in Las Vegas. The number of Android apps infected with malware was said to have soared from 80 apps in January, to more than 400 apps by the end of June.
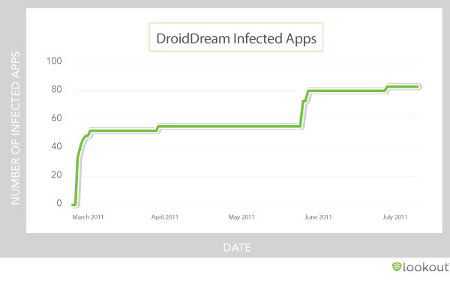
DroidDream attacks over time
Source: Lookout Mobile Security
(Click to enlarge)
"Attackers are deploying a variety of increasingly sophisticated techniques to take control of the phone, personal data, and money," says the Lookout study.
Lookout doesn't break-down the frequency of malware attacks by mobile operating system, but notes that Android is a growing target, due in part to its more open platform and Android Market online store.
"Malware and spyware are primarily targeting Android currently, though there are notable pieces of commercial spyware targeting iOS devices as well," says the study.
Lookout's free report includes aggregated data from more than 700,000 applications and 10 million devices worldwide.
Malware records phone calls
One recent data-chomping exploit reared its head in the form of an Android malware package, "Golddream.A," which records the conversations of those whose phones have been infected. Computer Associates security expert Dinesh Venkatesan reproduced the malware by showing how the Trojan logs all the details of incoming and outgoing calls and call duration in a text file.
The Trojan installs a configuration file that contains key information about the remote server and the parameters, says Venkatesan. It then can record the audio of phone calls, storing them on a phone's SD card in AMR (adaptive multi-rate) format.
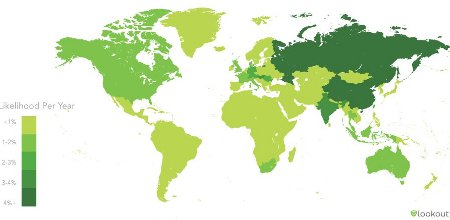
Estimated annual mobile malware infection rate in 2011 by nation (all operating systems)
Source: Lookout Mobile Security
(Click to enlarge)
Symantec, however, said Aug. 3 that fears of this malware were overblown because Android's hardware fragmentation. Differences among myriad devices from Samsung, HTC, Motorola and others limit the spread of this call recording threat. Symantec found this type of malware crashed on most of the devices used in its tests.
Malvertising and update attacks
Debate over the severity of the call recording malware aside, Lookout is seeing other creative malware in action, including threats it calls "malvertising" and "update attacks." In malicious advertising, perpetrators purchase mobile ads that point users toward a malicious website to trigger a dangerous payload download. GGTracker was the name of one malware program to use this tactic.
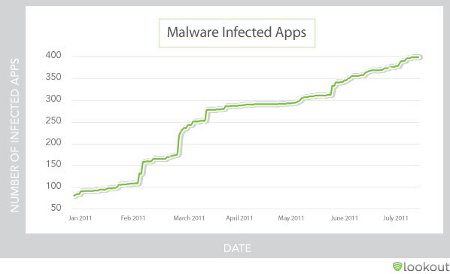
Malware infected mobile apps — all operating systems
Source: Lookout Mobile Security
(Click to enlarge)
Coming soon to a phone near you: mobile payment malware
Security aficionados and pundits may debate the notion of whether users should drop their Android phones and flee for the relative comfort of the more secure, locked down Apple iPhone and iTunes App Store. However, it might be more useful to look at what will drive future mobile threats on Android.
According to Lookout. mobile payment services, which include Google Wallet, Isis, and American Express' Serve, will be key attack vectors.
"The value of mobile payment transactions is projected to reach almost $630 billion by 2014, up from $170 billion in 2010," says the Lookout report. "Vendors, retailers, merchants, content providers, mobile operators, and banks are all actively establishing new payment services. Mobile payments create an attractive target for attackers, as they allow direct monetization of attacks."
According to Google, its Wallet service, which provides smartphone-based tap-and-pay services at participating retailers, offers sufficient security to keep credit card info safe. The system requires an Android-based Nexus S smartphone with a near field communication (NFC) chip with built in security.
The service hasn't launched, but when it does, attackers are sure to test it.
Clint Boulton is a writer for eWEEK.
This article was originally published on LinuxDevices.com and has been donated to the open source community by QuinStreet Inc. Please visit LinuxToday.com for up-to-date news and articles about Linux and open source.