Free app brings easy penetration testing to Android
Aug 8, 2011 — by Eric Brown — from the LinuxDevices Archive — viewsZimperium will soon release a penetration-testing app called Android Network Toolkit (Anti), ready to sniff our Wi-Fi vulnerabilities for good or evil, says Forbes. The software was shown at the DefCon hacking conference in Las Vegas, following a Black Hat security conference that featured presentations on a new DARPA Cyber-Fast Track project, the Shady RAT cyber-attack, and Facebook facial-recognition tools.
 Israeli security firm Zimperium, led by hacker Itzhak ("Zuk") Avraham, demonstrated the Android Network Toolkit (Anti) at the DefCon hacker conference in Las Vegas Aug. 5, and said it would be available on Android Market within the week, according to Andy Greenberg writing in Forbes.
Israeli security firm Zimperium, led by hacker Itzhak ("Zuk") Avraham, demonstrated the Android Network Toolkit (Anti) at the DefCon hacker conference in Las Vegas Aug. 5, and said it would be available on Android Market within the week, according to Andy Greenberg writing in Forbes.
The Anti app is designed as a basic, easy-to-use mobile penetration testing mechanism for searching out and demonstrating vulnerabilities in computer systems, says the story.
"We wanted to create a penetration testing tool for the masses," Zimperium founder Avraham, pictured above right in a Forbes shot, was quoted as saying. Zimperium bills itself as a security consultancy specializing in mobile security.
Available for free, or with a $10 corporate upgrade, Anti uses Wi-Fi to find and scan open networks and identify potential target devices on the networks, says the story. Its traceroute software, meanwhile, is said to reveal the IP addresses of remote servers.
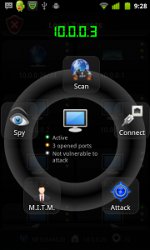 Anti options include the ability to eavesdrop on local devices or even attack via exploits collected in platforms like Metasploit or ExploitDB, says Forbes, which published the screenshot at left. While certainly useful for "white hat" security professionals who need to find vulnerabilities in order to protect resources, it could also be used by amateur spies and "black hat" malware attackers. (Professional black hats, meanwhile, likely have more sophisticated mobile tools at their disposal.)
Anti options include the ability to eavesdrop on local devices or even attack via exploits collected in platforms like Metasploit or ExploitDB, says Forbes, which published the screenshot at left. While certainly useful for "white hat" security professionals who need to find vulnerabilities in order to protect resources, it could also be used by amateur spies and "black hat" malware attackers. (Professional black hats, meanwhile, likely have more sophisticated mobile tools at their disposal.)
According to Forbes, Zimperium will ask users in its terms of service to limit their hacking to white hat penetration testing. (Yeah, that should do it.)
With its automated interface, Anti is somewhat similar to the Firesheep, proof-of-concept Firefox extension released last October, says the story. Firesheep, which let amateurs easily snoop on devices on unsecured Wi-Fi networks that connect to unencrypted web pages, was downloaded more than 1.7 million times, says Forbes. Aside from enabling possible nefarious exploits, "it also helped inspire both Twitter and Facebook to encrypt traffic to their site and prevent such eavesdropping," writes Greenberg.
Black Hat finishes up with Microsoft BlueHat prize, cyber-war warnings
As Fahmida Rashid reported from the Black Hat security conference in Las Vegas early last week in a preview, the show was set to feature discussions of SSL vulnerabilities, mobile attacks, Chrome OS security gaps, and "war-texting."
Also at Black Hat, as reported by WindowsForDevices, Microsoft announced a competition that will "reward security researchers … for developing innovative, new computer security protection technology." The "BlueHat Prize" competition will offer a $250,000 first prize, along with $50,000 and $10,000 awards, says the story.
Throughout the week, Rashid posted several other security-oriented stories linked to Black Hat on our sister site eWEEK. The following summaries link to the full stories:
- Black Hat organizer touts value of publicizing cyber-security research — In his keynote, Black Hat founder and director Jeff Moss called for IT departments to become more proactive in fighting malware. He also lauded the Department of Defense's "Cyber-Security Strategy" policy document and called for governments to publish similar documents to improve international collaboration against security threats.
- Ex-CIA official warns Black Hat attendees of coming cyber-war — In his keynote, Cofer Black, former director of the Central Intelligence Agency's Counterterrorist Center, warned that that cyber-war is an imminent threat, made more dangerous by the widespread ignorance of the subject among decision makers. The Stuxnet attack against Iranian centrifuges, which some have suggested was the work of the U.S. or Israel, "is the Rubicon of our future," said Black.
- Notorious Facebook spammer surrenders to FBI — Spam distributor Sanford Wallace voluntarily turned himself in to the FBI Aug. 4 after a July 6 indictment on phishing Facebook accounts and spamming the site. Wallace is accused of using half a million phished Facebook accounts to send 27 million spam messages in 2008 and 2009.
- Facial-recognition tools, Facebook photos threaten end to anonymity: study — Using off-the-shelf facial-recognition software and students' photos posted on Facebook, Alessandro Acquisiti, a Carnegie Mellon University researcher, showed Black Hat attendees how he was able to positively identify 30 percent of students walking around campus. Acquisti also searched dating sites for users within 50 miles of a zip code and correlated them with approximately 110,000 Facebook profiles of users who also lived in that same area.
- U.S. to fund hacking projects that thwart cyber-threats — At Black Hat, former L0pht hacker "Mudge" presented a new DARPA (Defense Advanced Research Projects Agency) initiative to fund hacking projects designed to help block cyber-threats. The Cyber-Fast Track project is intended to bridge the gap between hacker groups and government agencies, and will fund between 20 to 100 projects annually.
- Huge Shady RAT cyber-attack likely targeted 'thousands' more victims — McAfee identified 72 organizations hit by Operation Shady RAT, a five-year hacking campaign against government agencies, corporations and other high-profile organizations around the world, suspected of being was the work of a "single actor" directed by a nation-state. The research believes, however, that "thousands" more organizations or individuals may have been attacked.