Review: Yoggie Pico personal firewall
Jun 25, 2007 — by LinuxDevices Staff — from the LinuxDevices Archive — 5 views Yoggie's innovative Yoggie Pico may well be the first hardware firewall that is truly practical for mobile workers running Windows-based computers. The device appears to work well, except for a simplistic web-based user interface that may not satisfy technical users.
Yoggie's innovative Yoggie Pico may well be the first hardware firewall that is truly practical for mobile workers running Windows-based computers. The device appears to work well, except for a simplistic web-based user interface that may not satisfy technical users.
digg this story |
Hardware firewalls spare processor cycles on the main CPU, and offer better security, since they boot pristinely from read-only media each time. Other ultra-small form-factor hardware firewalls based on Linux include SnapGear's PCI-card firewall, the Arxceo Ally IP 100, and the Innominate mGuard.


Yoggie Pico
(Click each image to enlarge)
The Yoggie Pico, unveiled by Yoggie earlier this year, crams a complete Linux-based hardware firewall into a USB gadget little larger than a typical USB thumb drive. It works in conjunction with low-level Windows drivers that sit below the TCP/IP stack, commandeering network traffic from all interfaces, and routing it to USB and thence to the Yoggie.
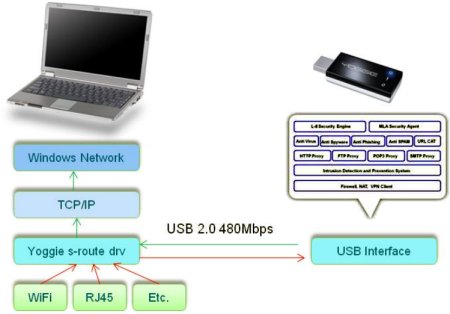
Yoggie Pico architecture diagram
(Click to enlarge)
The Yoggie is based on an Intel PXA270 SoC (system-on-chip), the same chip that serves as the primary application processor in many high-end smartphones. The device's “13-layer” firewall stack is said to provide:
- Anti-spam
- Anti-phishing
- Antispyware
- Antivirus
- Parent control system
- Transparent email proxies (POP3; SMTP)
- Transparent web proxies (HTTP; FTP)
- Intrusion detection system
- Intrusion prevention system
- Firewall
- Adaptive security policy
- Multi-layer security agent (Patent pending)
- “Layer-8” security engine (Patent pending)
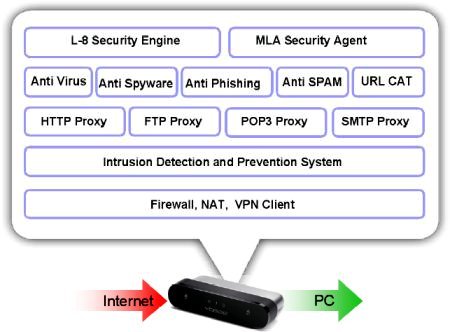
The Yoggie Pico's firewall stack
(Click to enlarge)
So, does it work? Can this tiny but powerful Linux-based system keep its cool under attack, when shoe-horned into a tiny USB key-sized enclosure?
Read on to find out.
Installation
The Yoggie comes with a fanfold quick-start guide that made installing the device very easy, at least on our AMD-based HP desktop system running Windows Vista. We didn't even have to reboot. The toughest part was disabling our existing anti-virus package — Symantec's Norton suite — as suggested by the quick-start guide.
Later, we re-enabled Norton's anti-virus capability while using the Yoggie, with no apparent adverse effects. Yoggie probably recommends disabling existing software to guard against potential conflicts with Kaspersky's anti-virus software, which comes bundled with the Pico. Since we didn't install Kaspersky, we decided to leave Norton on.
We chose not to install Kaspersky
(Click to enlarge)
The Pico booted in about 45 seconds, after which we installed Yoggie's Windows drivers using an installer application on the included CD. The installer appeared to install three or four separate Windows drivers, including a new RNDIS driver.
Yoggie's installer at work
(Click to enlarge)
Once the installer finished, a browser window popped open, and attempted to load a page from a non-routable IP address, using a non-well known port (176.12.1.1:8443, if memory serves). This address quickly redirected to http://yoggie.yoggie.com/, after which a security certificate error ensued — not so promising a sign, we thought.
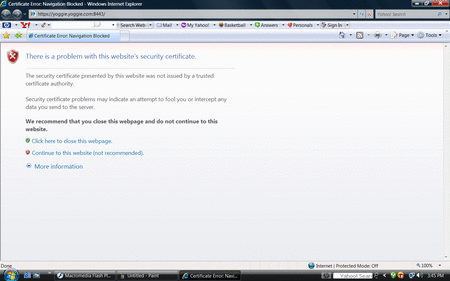
An unexpected security certificate error
(Click to enlarge)
The Yoggie's web-based user interface loaded successfully after we accepted the certificate for the session. After we changed our password, we got no further security certificate complaints from the browser. Meanwhile, all of the ports on our Windows Vista host started showing up as “filtered” when probed using nmap.
Initial impressions
The Yoggie's web interface comprises its only interface. This no doubt makes the device more robust. However, it also places a greater onus upon the interface to satisfy all users. With its colorful dashboard dials and 3D charts, we deemed Yoggie's simple-Simon web interface okay for pointy-haired bosses (PHBs), but felt that technical users might prefer fewer flashy 3D graphs and guages, and easier access to the Yoggie's actual log files and configuration settings.
For instance, the interface is width-limited to 800 pixels, making basic log perusal impossible without exporting to a spreadsheet.
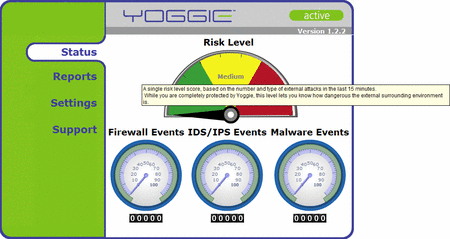
Ooh! Pretty…
(Click to enlarge)
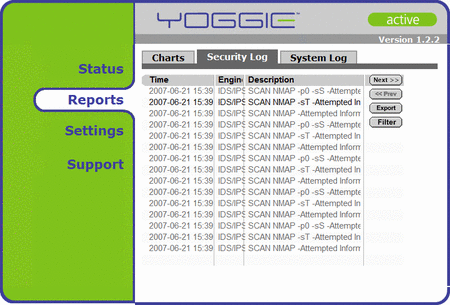
Reading log files is virtually impossible
(Click to enlarge)
Also nice would be more documentation built into the interface itself, and more access to system information, like CPU temperature and utilization.
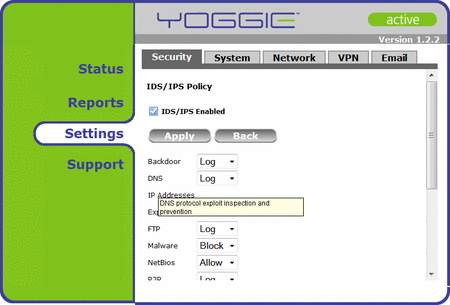
Settings help consists of terse bubble-text
(Click to enlarge)
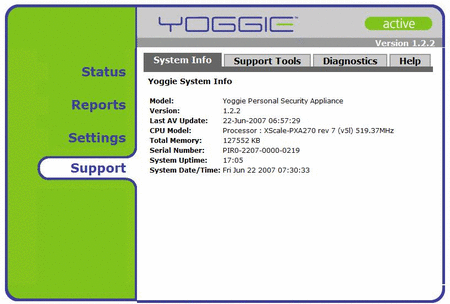
Static system info only
(Click to enlarge)
In fairness, the Yoggie represents an incredible feat of miniaturization, and the company probably had its hands full getting the basic building blocks into place. Now that the device is shipping, the browser-based user interface is likely to evolve quickly.
How robust is it?
We plugged a Linux laptop into the LAN, downloaded an updated set of security auditing scripts from Nessus.org, and pummeled our Vista host for about three hours. During the melee, the Yoggie blinked a lot, but largely kept its cool, never getting much hotter than a typical mobile phone. The Vista host failed to crash, despite warnings from Nessus.org about the potency of its scripts, and we continued using it to surf the Web, blissfully unaware of the attack except when we checked the Yoggie's dashboard, or noticed the wildly blinking lights on our switch.
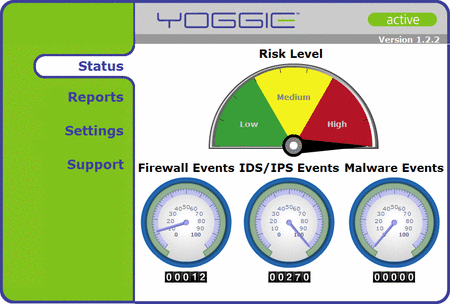
Nessus starts to peg Yoggie's dashboard guages
(Click to enlarge)
The Vista host survived the attack
(Click to enlarge)
Most reassuringly, the Vista host was still standing the next morning, and Nessus had nothing much to report about potential security holes found on the Vista host. Our limited background in security kept us from delving further into the Yoggie's efficacy as a firewall — for example by sending emails with virus-laden payloads. However, as far as we tested it, the Pico appeared to function as described by its manufacturer.
Conclusion
In summary, the Yoggie Pico appears to perform as advertised, silently thwarting attacks and exploits, and without requiring installation expertise. Unlike our ZoneAlarm and other software firewalls we have used, the device was refreshingly silent, never producing esoteric, jargon-rich error messages that made us stop and scratch our heads — after the initial browser certificate message, at least.
Technical users, though, may not appreciate the Yoggie's stoic nature. A richer Web interface with easier log file viewing and sorting might make the device more appealing to power users.
Availability
The Yoggie Pico is available now, priced at $180 with a year's subscription to updates, according to the company. Subscriptions will cost $30/year thereafter.
Distribution channels are being finalized, but should include big-box retailers like CompUSA and Fry's (Outpost.com). Dexxon Digital Storage, Inc. (DDSI) will handle distribution in North America.
Also available for $200 will be a “Pro” version targeting the enterprise market. It adds VPN features, and is designed to fetch firewall updates from a local enterprise server rather than from Yoggie's central servers.
This article was originally published on LinuxDevices.com and has been donated to the open source community by QuinStreet Inc. Please visit LinuxToday.com for up-to-date news and articles about Linux and open source.