Open source phone audits networks
Sep 22, 2008 — by Eric Brown — from the LinuxDevices Archive — 8 views A startup called NeoPwn has customized the OpenMoko Neo FreeRunner to act as a network security penetration testing device. Booting BackTrack Linux off a MicroSD card to perform penetration testing (pentesting), the NeoPwn is the first network auditing distribution for a mobile phone, claims the… company.
A startup called NeoPwn has customized the OpenMoko Neo FreeRunner to act as a network security penetration testing device. Booting BackTrack Linux off a MicroSD card to perform penetration testing (pentesting), the NeoPwn is the first network auditing distribution for a mobile phone, claims the… company.
(Click for larger view of the Neo FreeRunner, which is physically identical to the NeoPwn)
When the BackTrack card is not installed for pentesting, the NeoPwn behaves as a normal Openmoko Neo Freerunner phone, running any of the open-source phone's supported distributions. Manufactured by FIC Inc., the highly hackable Neo FreeRunner incorporates a 400MHz Samsung S3C2442 (ARM9 core), 128MB of RAM, 256MB of flash, and a 2.8-inch 640 x 480 TFT display. Additional features include WiFi, Bluetooth, GPS, accelerometers, and a 2.5G tri-band GPRS/GSM cellular modem.
OpenMoko not only opened the phone's source code, but also posted schematics for the phone, enabling users to modify the physical device. Already, the Communications Research Center Canada (CRC) has produced a prototype called the Openmokast that uses a larger case and digital TV receiver to allow the device to receive datacasts.
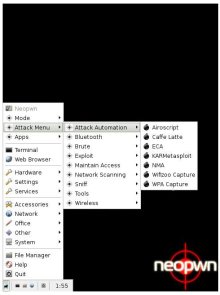
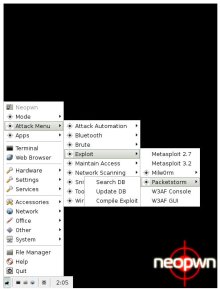
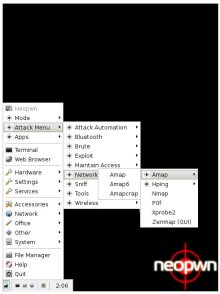
NeoPwn pentesting options
(Click any to enlarge)
Unlike the OpenMokast, the NeoPwn does not physically alter the basic design, but adds onto it with its MicroSD-based distribution. It also bundles a USB-based WiFi card, which is required because the current firmware for the Neo FreeRunner's internal WiFi does not support monitoring or wireless packet injection applications, says the company. Additional hardware extensions include a USB cable, hub, extension, and mini-B connector.
According to the NeoPwn FAQ, the device “is quite capable of performing many of the same network auditing and penetration tests that a mobile notebook can.” It has been benchmarked by NeoPwn to crack a WEP-encrypted network in a little over five minutes with a connected client, and about 14 minutes on a clientless network, says the company.

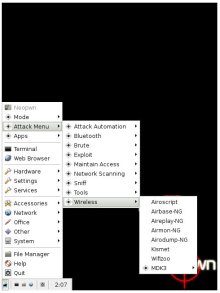
More NeoPwn options
(Click any to enlarge)
Stated the company in a Slashdot teaser post, “There have been other commercial grade pocket penetration testing platforms in the past, however they lacked the ability of wireless packet injection and open source programming. These devices also carry a hefty pricetag.” By comparison, the NeoPwn adds $400 to the cost of the $300 Neo FreeRunner, with prices ranging from $700 to $1,000, depending on MicroSD memory (2GB, 4GB, or 8GB) and the type of bundled USB WiFi card. Phoneless bundles are also available for users who already own a Neo FreeRunner.
NeoPwn OS
The phrase “pwn” derives from the word “own,” meaning to gain control of a network or system. It probably originated as a typo, when the adjacent letters 'p' and 'o' were juxtaposed on a standard QWERTY keyboard. However, the typo stuck, and has become a standard computer jargon term.
The NeoPwn OS is based on a Linux 2.6.24 kernel and BackTrack Linux, a full Debian (ARMEL) GNU/Linux distribution released as a live CD. Resulting from the merger of two Knoppix-based distros: WHAX and the Auditor Security Collection, BackTrack is said to include over 300 security tools, including Aircrack, Maltego, Metasploit, SAINT, attack, and numerous other attack, sniffing, and network exploitation utilities. The full list of NeoPwn OS applications may be found here.
 NeoPwn architecture (Click to enlarge) |
The key advantage of a portable pentester is the level of discretion it affords, says NeoPwn. “You will have the ability to discretely arm yourself with a device that will fit in a pocket to test various aspects of your client's network — going places where being promiscuous and undetected is essential,” says NeoPwn.
The obvious drawback, however, is the lack of a QWERTY keyboard. NeoPwn tries to compensate with a virtual QWERTY keyboard, as well as “automation scripts, dialogs, and a point and pwn menu,” says the company. For example, the NeoPwn is said to incorporate GUI dialogs for WEP cracking (client and clientless), Caffe Latte Attack, KARMetasploit, and WPA handshake capturing.
In addition to offering the base Neo FreeRunner specs, the NeoPwn is said to offer:
- 2GB, 4GB, or 8GB microSD preloaded with NeoPwn OS, a custom Linux 2.6.24 kernel, and open-source pentesting tools suite
- Mini-B to USB connector (OTG), enabling USB host mode
- Two- or four-port unpowered USB hub with rechargeable batteries (self-powered version “coming soon”)
- USB extension with male-to-female adapter
- USB WLAN card, either RT73-based (Basic model) or the larger Alfa AWUS036H 500mW (Standard and Extreme models); bundled drivers support other WiFi cards
- Optional UMTS/HSPDA modem with tri-band HSUPA/HSDPA (850/1900/2100MHz) and quad-band EDGE/GPRS (850/900/1800/1900MHz)
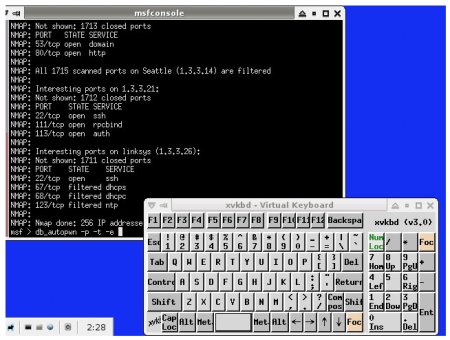
NeoPwn offers a virtual keyboard
(Click to enlarge)
Availability
NeoPwn is taking pre-orders for its pentesting phone, with shipments scheduled to begin on Oct. 1. The prices are as follows for complete bundles of software and accessories, which include a backup DVD, OTG-to-USB adapter, portable USB hub, USB cable, documentation, and support:
- NeoPwn Basic — 2GB MicroSD card and a RT73-based USB WiFi card — $700 ($300 without phone)
- NeoPwn Standard — 4GB MicroSD card and an Alfa AWUS036H 500mW USB WiFi card — $800 ($400 without phone)
- NeoPwn Extreme — 4GB MicroSD card and an Alfa AWUS036H 500mW USB WiFi card — $1,000 ($600 without phone)
NeoPwn also sells software-only systems without phone or accessories, but including DVD, support, and documentation for $80 (Basic), $100 (Standard), and $130 (Extreme). Custom hardware and software configurations are also available, says the company.
This article was originally published on LinuxDevices.com and has been donated to the open source community by QuinStreet Inc. Please visit LinuxToday.com for up-to-date news and articles about Linux and open source.